Close
Close
SSDLC stands for Secure Software Development Lifecycle. It is a framework or methodology incorporating security considerations and practices throughout the software development process. SSDLC aims to ensure that security is integrated into every phase of software development, from initial planning and design to coding, testing, deployment, and maintenance.
SSDLC recognizes the importance of proactive security measures and aims to identify and address potential security vulnerabilities and risks early in development. By incorporating security from the beginning, organizations can reduce the likelihood of security breaches, data leaks, and other security incidents.
The specific activities and practices within SSDLC may vary depending on the organization and development process followed. However, common elements of SSDLC typically include:
Threat modeling: Identifying potential threats and risks to the software application and its environment.
Security requirements: Defining and incorporating specific security requirements into the software development process.
Secure coding practices: Following secure coding guidelines and best practices to minimize vulnerabilities.
Security testing: Conduct regular security testing throughout the development lifecycle, including vulnerability scanning, penetration testing, and code review.
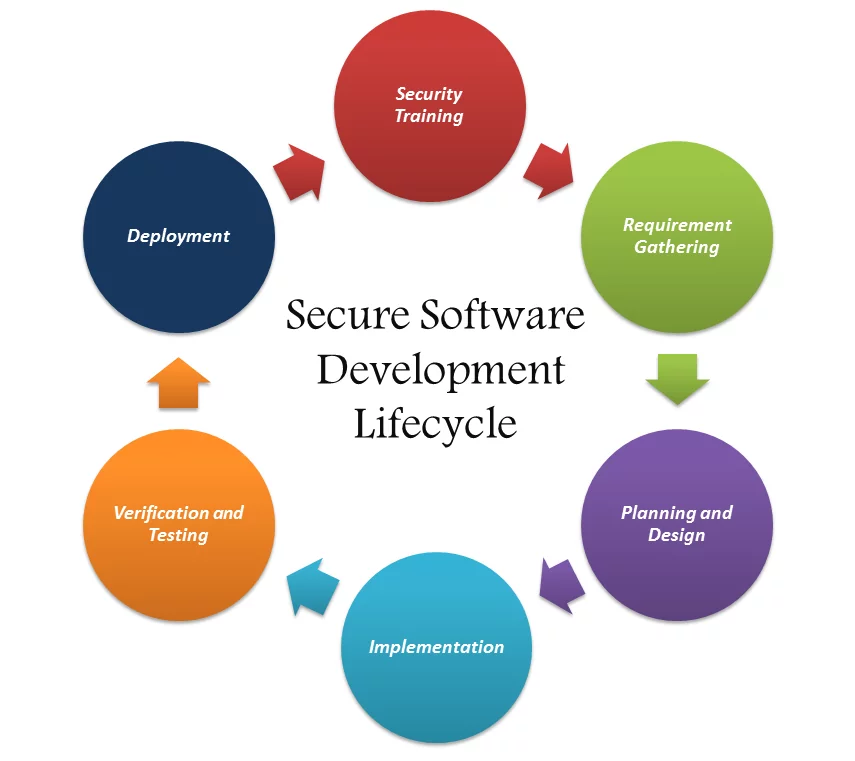
Security training and awareness: Educating developers and stakeholders about secure coding practices, common vulnerabilities, and security threats.
Secure deployment: Implementing secure deployment practices to ensure the software is securely installed and configured in its production environment.
Ongoing monitoring and maintenance: Continuously monitoring the software application for security issues and applying necessary updates and patches.
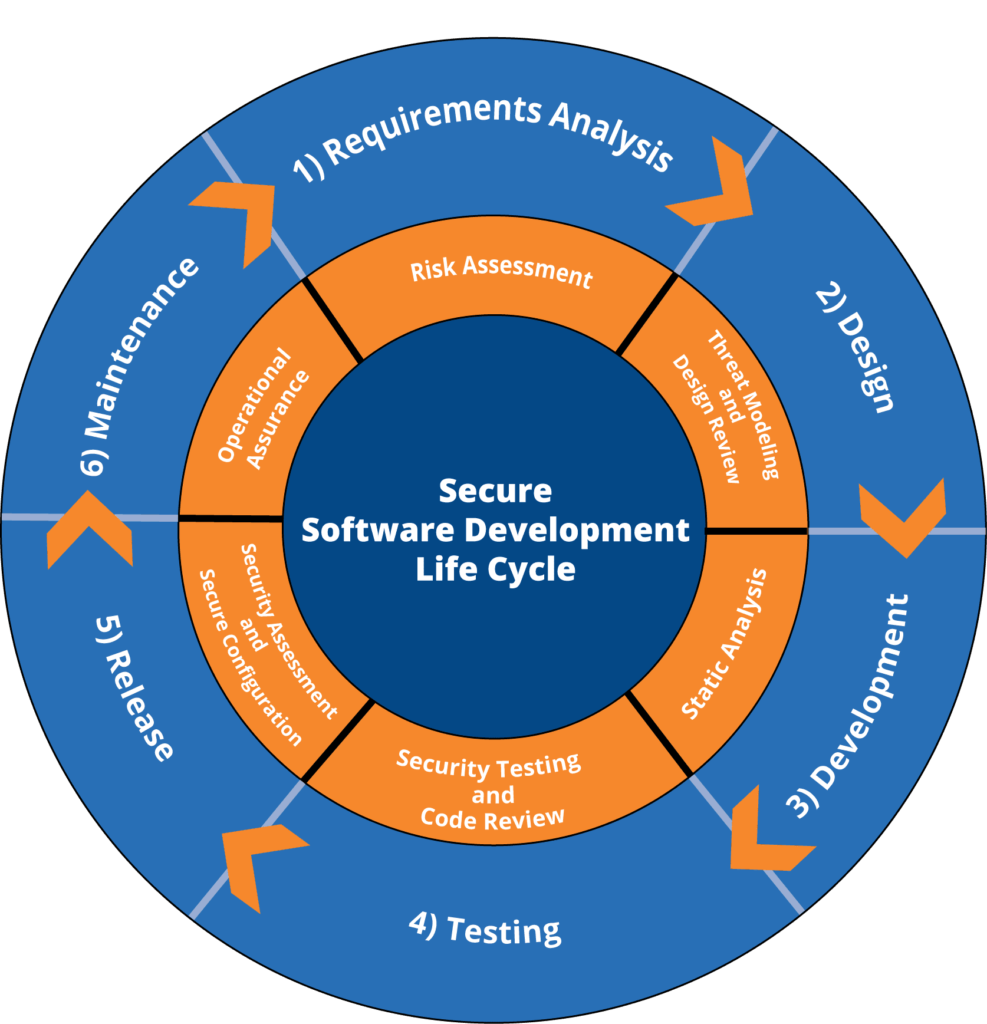
Phases explained in the Cybersecurity Secure Software Development Life Cycle (SSDLC):
Planning:
In the planning phase, the overall objectives and requirements for the software application are defined. This includes identifying the purpose of the application, its intended users, and the desired functionality. From a cybersecurity perspective, this phase involves conducting a risk assessment to identify potential threats and vulnerabilities. Risk mitigation strategies are developed, such as defining security controls and establishing security requirements. The planning phase sets the foundation for the secure development of the software application.
Development:
The development phase involves actually building the software application based on the requirements and design specifications outlined in the planning phase. From a cybersecurity perspective, this phase focuses on implementing security controls and best practices. This includes using secure coding techniques, applying encryption where needed, properly validating user input, and implementing access controls. Security features like authentication, authorization, and session management are also implemented during this phase. The development phase plays a critical role in ensuring that the software application is built with security in mind.
Testing:
The testing phase is where the software application is thoroughly tested for its functionality, performance, and security. From a cybersecurity perspective, security testing is a crucial aspect of this phase. It involves conducting various tests to identify vulnerabilities and weaknesses in the application. This can include penetration testing, vulnerability scanning, code reviews, and security-focused testing techniques. The objective is to identify any security flaws or weaknesses that could be exploited by attackers. Any identified vulnerabilities are addressed and remediated before moving on to the next phase.
Deployment:
The deployment phase involves making the software application available for use by the intended users. From a cybersecurity perspective, this phase focuses on ensuring that the deployment environment is secure. This includes securely configuring the servers and network infrastructure, implementing secure transfer protocols, and hardening the overall system. Access controls are also set up to ensure that only authorized individuals can access the application and its resources. Proper monitoring and logging mechanisms are put in place to detect and respond to any security incidents.
Maintenance:
The maintenance phase is an ongoing process that involves supporting and maintaining the software application after it has been deployed. From a cybersecurity perspective, this phase includes applying regular software updates and patches to address any newly discovered vulnerabilities. It also involves monitoring the application for any security events and responding to them promptly. Additionally, periodic security assessments and audits are conducted to ensure the application’s security posture is maintained. The maintenance phase is crucial for keeping the software application secure throughout its lifecycle.
Archiving:
The archiving phase is where the software application is retired or decommissioned. From a cybersecurity perspective, this phase involves securely disposing of any sensitive data or information associated with the application. This may include securely deleting databases, removing user data, and ensuring that any backups or archives are securely managed. It is important to properly handle the decommissioning process to prevent any potential security risks or data breaches in the future.