Close
Close
The role of the Chief Information Security Officer (CISO) is multifaceted, and as cyber threats continue to grow in complexity, the importance of this position in an organization has become more pronounced.
The functions of a CISO:
Strategic Leadership: The CISO develops and communicates a strategic vision for information security, aligning with the organization’s broader goals. They ensure that the security strategy is adaptive to evolving threats and aligns with business objectives.
Policy and Standards Development: They Maintain and update the organization’s security policies, procedures, and standards that guide how the organization approaches security and risk.
Security Program Oversight: They oversee developing and implementing an organization-wide security program that includes cybersecurity, physical security, and insider threat prevention.
Risk Management: The CISO identifies and evaluates security risks, ensuring an effective risk management process is in place. They help the organization understand the potential security implications of its decisions.

Incident Management: They oversee creating an incident response plan and lead the response to security incidents, ensuring effective coordination, communication, and recovery.
Awareness and Training: A crucial part of security is ensuring that all employees are aware of and trained on security best practices and policies.
Security Operations and Architecture: They ensure that security solutions (like firewalls, intrusion detection systems, and end-point protection) are effectively deployed and maintained.
Regulatory and Compliance Management: The CISO ensures that the organization adheres to external regulations (like GDPR, HIPAA, etc.) and internal security policies.
Liaison: Acts as the bridge between non-technical executive staff and technical IT staff, translating complex security concepts into business terms.
Characteristics Required for a CISO:
Technical Expertise: A strong understanding of IT infrastructure, architectures, and security technologies.
Strategic Thinking: Ability to align security initiatives with the organization’s objectives and risk appetite.
Leadership Skills: They must lead teams, influence organizational culture, and serve as the voice of security.
Effective Communication: Ability to convey complex security issues in business terms to the board, other executives, and all levels of staff.
Problem-Solving: A CISO must be agile and creative in developing solutions as threats evolve.
Integrity: Given the sensitive nature of the role, a high degree of trustworthiness and ethical conduct is essential.
Risk Management: Ability to identify, evaluate, and mitigate risks in line with business objectives.


Importance of a CISO in an Organization:
Protect Organizational Assets: This includes both tangible assets (like systems or data) and intangible ones (like reputation).
Compliance: Ensures that the organization meets regulatory and legal requirements, avoiding potential fines and legal actions.
Incident Management: An effective response can mean the difference between a contained incident and a major breach.
Trust: Customers, partners, and stakeholders trust organizations prioritizing security more.
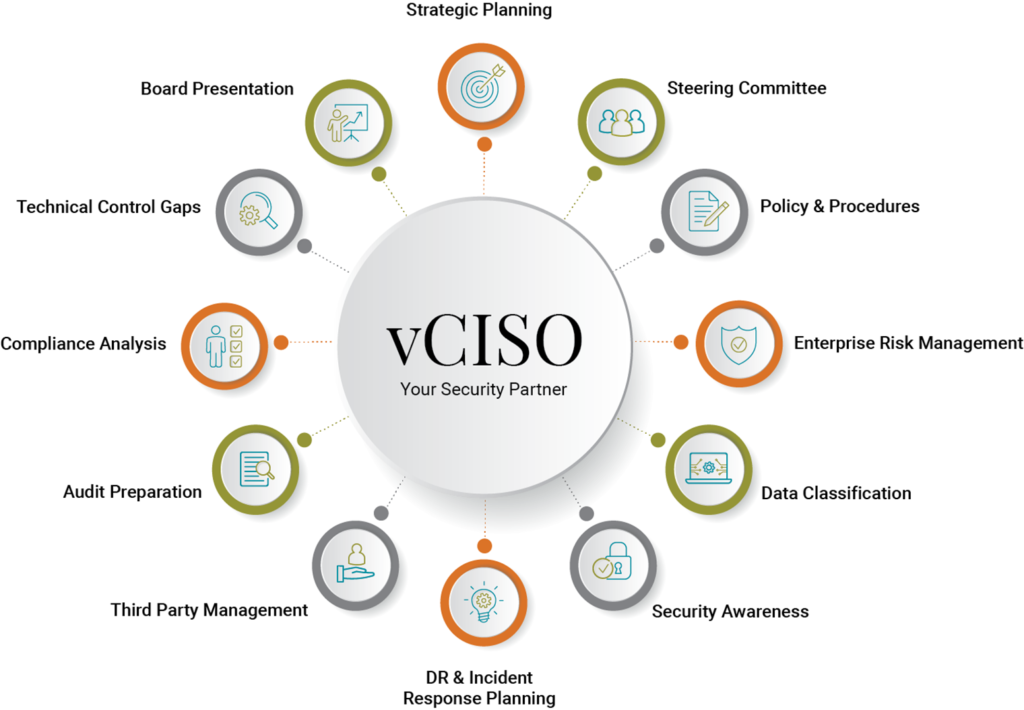
CISO as-a-Service (CISOaaS) or Virtual CISO (vCISO)ompliance :
CISOaaS or vCISO refers to an outsourced service where an individual or a firm provides CISO functions to organizations on a temporary basis or as an ongoing service. This model is particularly beneficial for organizations that cannot afford or do not require a full-time CISO.
The key attributes and Advantages of CISOaaS Includes:
Flexibility: Organizations can engage a vCISO for a specific period, for a specific project, or on an ongoing but part-time basis.
Cost-Effective: Smaller organizations can access top-tier security expertise without the costs associated with a full-time executive salary and benefits.
Diverse Expertise: Firms offering CISOaaS often have a team of experts with varied backgrounds, providing a broader range of expertise.
External Perspective: An external vCISO can provide an unbiased view of the organization’s security posture.
Quick Deployment: In situations that require immediate attention, a vCISO can be engaged quickly.
Key Differences between CISO and CISOaaS:
Employment Structure: A traditional CISO is a full-time, in-house executive, while a vCISO is typically a contractual or part-time external service.
Cost: Hiring a full-time CISO can be expensive, especially when considering benefits, bonuses, and other overheads. CISOaaS offers a way to get expert services, often at a fraction of that cost.
Commitment: With a traditional CISO, there’s a long-term commitment, whereas with CISOaaS, the commitment can be project-based, temporary, or adjustable based on the organization’s needs.
Perspective: An in-house CISO may be deeply aligned with company culture and internal processes, potentially creating blind spots. An external vCISO can bring a fresh, outside perspective.
Resource Availability: While a CISO is one individual, a CISOaaS firm might provide access to a team of experts with diverse specializations.
Integration with company culture: An in-house CISO may have a deeper understanding of the company’s culture, politics, and nuances, allowing for smoother integration of security initiatives. A vCISO may need some time to familiarize themselves with the organization’s intricacies.