Close
Close




Securesee cybersecurity intelligence military-grade consult service is designed to help you protect your organization from the ever-growing threat of cyber-attacks. The company offers the most comprehensive range of high-quality, affordable cybersecurity consulting and services solutions available to businesses with various services that can be tailored to your specific needs, including threat assessments, vulnerability assessments, incident response planning, CISO-as-a-service, Compliance, training & awareness programs, and much more. Our mission and dedication are to provide our clients with the best possible up-to-date on the latest cybersecurity threats and ensure their organization is safe and trusted.
Securesee integrates core cybersecurity principles to protect organizations from internal and external threats. Our clients receive reliable logistical and implementation services from selective leading providers to assess vulnerability, software planning, security programs, compliance considerations, and more. Our mission and dedication are to protect our clients with the best possible up-to-date cybersecurity measures and ensure that their organization is safe and trusted. We provide our clients with the sturdiest cybersecurity framework to overcome existing and evolving threats while securing data and assets.
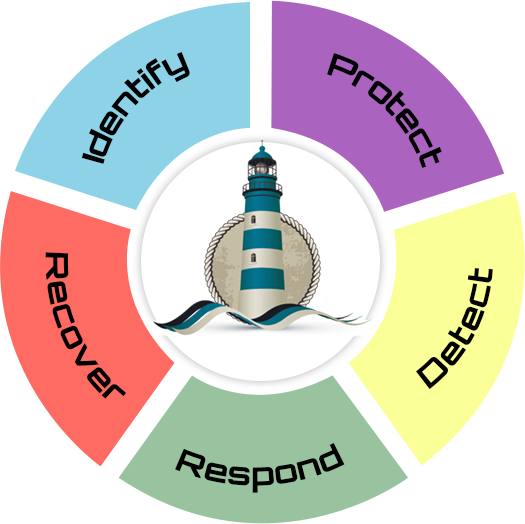
Assessing existing and possible cybersecurity threats is an effective risk management strategy, protecting your organization’s data, assets, operations, and potential. Identifying is a crucial framework pillar, merging cybersecurity and business needs. Estimating and establishing cyber resilience includes implementation considerations, asset management, risk analysis, risk management strategies, and governance to plan a secure foundation. Securesee fulfills identification by extracting critical information such as internal and external risk assessment and management strategies, prevalent cybersecurity operations, vulnerabilities, and potential threats. Securesee views identification as the foundation for navigating, drafting, implementing, and monitoring the efficacy of cybersecurity services. Identification is a premise to ensure data and assets’ technical and physical safety, producing a sustainable bedrock of stakeholder relations and facilitating other essential organizational practices that improve reliance. Securesee provides an organization with the leverage of business-centric cybersecurity, constructing a path to evolving potential with innovation.
Results from identification through risk assessment and cyber threat analysis are the foundation of cybersecurity policies and procedures that fulfill the purpose of protection. Protection has multidimensional impacts, including securing critical infrastructure from malware, breach, and other cyber threats. Protection is a proactive framework that inculcates preventative measures. These measures become a governing principle of the data security and protection outline. Protection policies or procedures integrate assessment with tangible data security outputs to limit the impact of a potential cyber threat event. The consequences of these actions are part of cyber resilience, expanding an organization’s scope through reliance, integrity, and transparency. The protective technologies implemented as measures are critical and define cybersecurity. General protective technologies include the qualities of a zero-trust model, blockchain, authentication, deep learning, and behavioral analysis. Securesee assures next-generation security through analysis, reporting, and proactive action, securing an organization from the most advanced attacks.
Cyber anomalies are invincible with innovation. Timely detection is the key to mitigating these anomalies and disallowing predictable ones. An efficient response rate lies at the core of reliability. Securesee follows a three-point approach to tackle a delayed response rate: detect, monitor, and evolve. Tracking and reporting is a constructive procedure to ensure timely detection. Securesee uses dexterous antivirus software as a barrier to any potential cyber threat. A timely alert within this system ensures detection within an appropriately defined interval after identifying the risk. Monitoring systems, networks, and antivirus software is part of a functional cyber management framework. Securesee’s alert operations recognize suspicious behavior and unauthorized changes to a network or system and implement the appropriate response strategy. A customizable yet versatile structure stands frail when opposed to an evolved threat. Securesee’s innovative approach integrates evolution to keep up-to-date with the latest cybersecurity threats.
Securesee establishes an effective chain of command implemented during a cybersecurity event. Inevitable or predictable attacks demand identification, detection, communication, and recovery strategies. Unforeseeable cybersecurity attacks demand a swift and nifty transmission in the order that serves urgency best. With a conscientious and collaborative approach, Securesee aims to tackle challenges like delayed response rates effectively. Another facet of response involves activities undertaken after successfully mitigating a cybersecurity attack. Upon the recovery from an incident, a response framework to monitor and examine the phenomenon is essential as an effective assessment strategy to protect. To decrease the role of human error stemming from inappropriate management of cybersecurity networks, misdemeanors, and more, Securesee undertakes system security measures with a collaborative approach. Securesee provides and implements its core competencies to serve an organization’s cybersecurity needs. As an independent operator, Securesee acts as an administrator and executive of powerhouse CIRTs.
Even sturdy critical IT infrastructure can collapse under cybersecurity threats. Recovery, as Securesee’s principle, means to ensure the implementation of mitigation strategies when these circumstances, predictable or not, occur. As recovery strategies minimize the impact of a cybersecurity breach, the response rate increases. Step-by-step, recovery entails timely identification of cyber threats, relevant communication, minimizing the impact of a cybersecurity breach, returning and recovering data and systems, and following recovery procedures. The reports generated through an analysis of the cybersecurity threat occurrence transform into a baseline for techniques and technologies used to protect information systems, networks, and devices. For businesses, recovery is crucial to minimize a security incident’s impact and resume normal operations as quickly as possible. This often involves identifying and containing the source of the attack, assessing the damage, and restoring impacted systems, data, and processes. Effective recovery plans and processes help businesses ensure the continuity of their operations and reduce the risk of long-term harm to their reputation and financial standing.
Assessing existing and possible cybersecurity threats is an effective risk management strategy, protecting your organization’s data, assets, operations, and potential. Identifying is a crucial framework pillar, merging cybersecurity and business needs. Estimating and establishing cyber resilience includes implementation considerations, asset management, risk analysis, risk management strategies, and governance to plan a secure foundation. Securesee fulfills identification by extracting critical information such as internal and external risk assessment and management strategies, prevalent cybersecurity operations, vulnerabilities, and potential threats. Securesee views identification as the foundation for navigating, drafting, implementing, and monitoring the efficacy of cybersecurity services. Identification is a premise to ensure data and assets’ technical and physical safety, producing a sustainable bedrock of stakeholder relations and facilitating other essential organizational practices that improve reliance. Securesee provides an organization with the leverage of business-centric cybersecurity, constructing a path to evolving potential with innovation.
Cyber anomalies are invincible with innovation. Timely detection is the key to mitigating these anomalies and disallowing predictable ones. An efficient response rate lies at the core of reliability. Securesee follows a three-point approach to tackle a delayed response rate: detect, monitor, and evolve. Tracking and reporting is a constructive procedure to ensure timely detection. Securesee uses dexterous antivirus software as a barrier to any potential cyber threat. A timely alert within this system ensures detection within an appropriately defined interval after identifying the risk. Monitoring systems, networks, and antivirus software is part of a functional cyber management framework. Securesee’s alert operations recognize suspicious behavior and unauthorized changes to a network or system and implement the appropriate response strategy. A customizable yet versatile structure stands frail when opposed to an evolved threat. Securesee’s innovative approach integrates evolution to keep up-to-date with the latest cybersecurity threats.
Even sturdy critical IT infrastructure can collapse under cybersecurity threats. Recovery, as Securesee’s principle, means to ensure the implementation of mitigation strategies when these circumstances, predictable or not, occur. As recovery strategies minimize the impact of a cybersecurity breach, the response rate increases. Step-by-step, recovery entails timely identification of cyber threats, relevant communication, minimizing the impact of a cybersecurity breach, returning and recovering data and systems, and following recovery procedures. The reports generated through an analysis of the cybersecurity threat occurrence transform into a baseline for techniques and technologies used to protect information systems, networks, and devices. For businesses, recovery is crucial to minimize a security incident’s impact and resume normal operations as quickly as possible. This often involves identifying and containing the source of the attack, assessing the damage, and restoring impacted systems, data, and processes. Effective recovery plans and processes help businesses ensure the continuity of their operations and reduce the risk of long-term harm to their reputation and financial standing.
Results from identification through risk assessment and cyber threat analysis are the foundation of cybersecurity policies and procedures that fulfill the purpose of protection. Protection has multidimensional impacts, including securing critical infrastructure from malware, breach, and other cyber threats. Protection is a proactive framework that inculcates preventative measures. These measures become a governing principle of the data security and protection outline. Protection policies or procedures integrate assessment with tangible data security outputs to limit the impact of a potential cyber threat event. The consequences of these actions are part of cyber resilience, expanding an organization’s scope through reliance, integrity, and transparency. The protective technologies implemented as measures are critical and define cybersecurity. General protective technologies include the qualities of a zero-trust model, blockchain, authentication, deep learning, and behavioral analysis. Securesee assures next-generation security through analysis, reporting, and proactive action, securing an organization from the most advanced attacks.
Securesee establishes an effective chain of command implemented during a cybersecurity event. Inevitable or predictable attacks demand identification, detection, communication, and recovery strategies. Unforeseeable cybersecurity attacks demand a swift and nifty transmission in the order that serves urgency best. With a conscientious and collaborative approach, Securesee aims to tackle challenges like delayed response rates effectively. Another facet of response involves activities undertaken after successfully mitigating a cybersecurity attack. Upon the recovery from an incident, a response framework to monitor and examine the phenomenon is essential as an effective assessment strategy to protect. To decrease the role of human error stemming from inappropriate management of cybersecurity networks, misdemeanors, and more, Securesee undertakes system security measures with a collaborative approach. Securesee provides and implements its core competencies to serve an organization’s cybersecurity needs. As an independent operator, Securesee acts as an administrator and executive of powerhouse CIRTs.






